ICISPC 2022
ICISPC 2022 conference
ICISPC 2022
was held online during July 22-24, 2022.
Through the two days of the conference,
we are privilege to have with us four
distinguished speakers who will deliver
their keynote speeches: Prof. Xiang-Gen
Xia, from University of Delaware, USA;
Prof. Shrikanth (Shri) Narayanan, from
University of Southern California, USA;
Prof. Chip Hong Chang, from Nanyang
Technological University, Singapore, and
Prof. Minghui Li, University of Glasgow,
UK.
Good news, ICISPC2022 proceedings are indexed by EI Compendex and Scopus.
|
|
|
|
|
|
Session 1: Signal Analysis and Estimation
Presenter: Xibo Zhou
Harbin Institute of Technology, China
Analyze the Sea Clutter Frequency of multi-receiving ships for
Distributed Shipborne HF Hybrid Sky-Surface Wave Radar
Session 2: Intelligent Image Analysis and Processing
Presenter: Yifan Zhai
Waseda University, Japan
Multi-scale and Bi-path Method Based on Image Entropy and CNN for Fast
CU Partition in VVC
Session 3: Computer Model and Virtual Technology
Presenter: Jiaheng Zhang
Nanyang Technological University, Singapore
Topic-aware Networks for Answer Selection
Session 4: Electronics and Communication Engineering
Presenter: Abd Al Rahman Faour
Lebanese International University, Lebanon
SCR: A Sub-clustering Approach for Redundancy Reduction Based on Data
Correlation in WSNs
Speakers of ICISPC2022

Prof. Xiang-Gen Xia
Fellow of IEEE
University of Delaware, USA
Biography:
Xiang-Gen Xia is the Charles Black Evans
Professor, Department of Electrical and
Computer Engineering, University of
Delaware, Newark, Delaware, USA. Dr. Xia
was the Kumar’s Chair Professor Group
Professor (guest) in Wireless
Communications, Tsinghua University,
during 2009-2011, the Chang Jiang Chair
Professor (visiting), Xidian University,
during 2010-2012, and the WCU Chair
Professor (visiting), Chonbuk National
University, during 2009-2013. He
received the National Science Foundation
(NSF) Faculty Early Career Development
(CAREER) Program Award in 1997, the
Office of Naval Research (ONR) Young
Investigator Award in 1998, the
Outstanding Overseas Young Investigator
Award from the National Nature Science
Foundation of China in 2001, and the
Information Theory Outstanding Overseas
Chinese Scientist Award from the Chinese
Information Theory Society of Chinese
Institute of Electronics in 2019. Dr.
Xia was the General Co-Chair of ICASSP
2005 in Philadelphia. He is a Fellow of
IEEE. His current research interests
include space-time coding, MIMO and OFDM
systems, digital signal processing, and
SAR and ISAR imaging. He is the author
of the book Modulated Coding for
Intersymbol Interference Channels (New
York, Marcel Dekker, 2000).
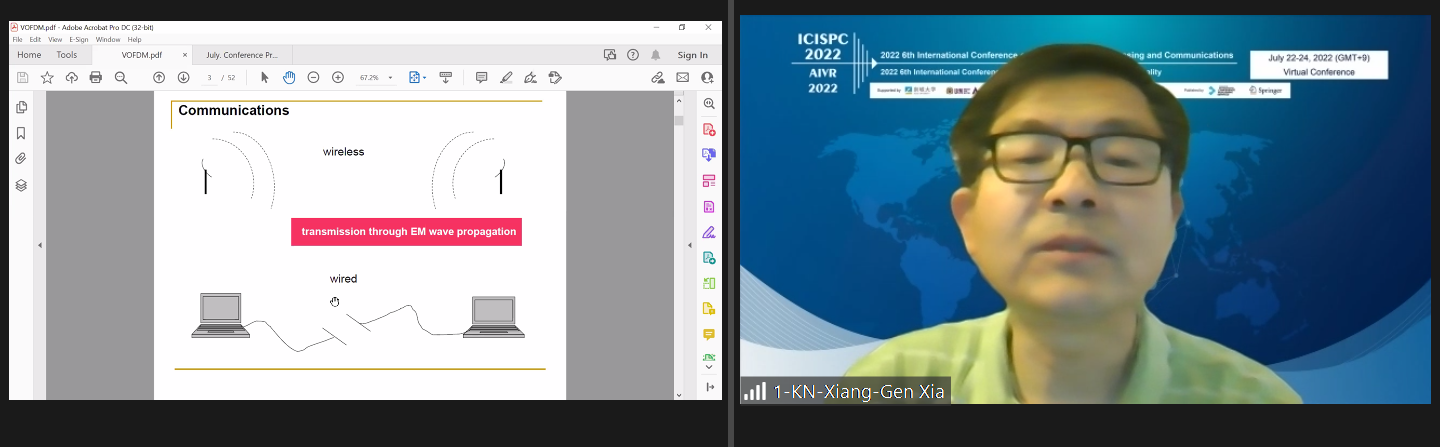
Title: Vector OFDM Systems
Abstract: Over the past decades, dealing with intersymbol interference (ISI) has been the main subject in physical layer communications systems, such as in wireline computer modem designs and wireless cellular and WiFi systems. The increasing of a channel bandwidth causes the increasing of the ISI channel length. In this talk, I will talk about single antenna vector OFDM (VOFDM) systems first appeared in ICC 2000. VOFDM is a bridge of OFDM and single carrier frequency domain equalizer (SC-FDE) that are the downlink and uplink, respectively, in LTE. VOFDM provides the flexibility of choosing a level of ISI for any fixed channel length (or channel bandwidth). I will talk about linear receivers and their properties for VOFDM systems. Also, the transmitted signals of VOFDM and the recent OTFS are identical.

Prof. Shrikanth (Shri) Narayanan
Fellow of NAI, ASA, IEEE, ISCA, APS, AAAS, and AIMBE
University of Southern California, USA
Biography: Shrikanth (Shri) Narayanan is
University Professor and
Niki & C. L. Max Nikias Chair in Engineering at the University of Southern California, where he is Professor of Electrical & Computer Engineering, Computer Science, Linguistics, Psychology, Neuroscience, Pediatrics, and Otolaryngology—Head & Neck Surgery, Director of the Ming Hsieh Institute and Research Director of the Information Sciences Institute. Prior to USC he was with AT&T Bell Labs and AT&T Research. His research focuses on human-centered information processing and communication technologies. He is a Guggenheim Fellow and a Fellow of the National Academy of Inventors, the Acoustical Society of America, IEEE, ISCA, the American Association for the Advancement of Science (AAAS), the Association for Psychological Science, and the American Institute for Medical and Biological Engineering (AIMBE). He is a recipient of several honors including the 2015 Engineers Council’s Distinguished Educator Award, a Mellon award for mentoring excellence, the 2005 and 2009 Best Journal Paper awards from the IEEE Signal Processing Society and serving as its Distinguished Lecturer for 2010-11, a 2018 ISCA CSL Best Journal Paper award, and serving as an ISCA Distinguished Lecturer for 2015-16, Willard R. Zemlin Memorial Lecturer for ASHA in 2017, and the Ten Year Technical Impact Award in 2014 and the Sustained Accomplishment Award in 2020 from ACM ICMI. He has published over 900 papers and has been granted eighteen U.S. patents. His research and inventions have led to technology commercialization including through startups he co-founded:
Behavioral Signals Technologies focused on the telecommunication services and AI based conversational assistance industry and Lyssn
focused on mental health care delivery, treatment and quality assurance. He serves as the inaugural Vice President–Education for the IEEE Signal Processing Society.
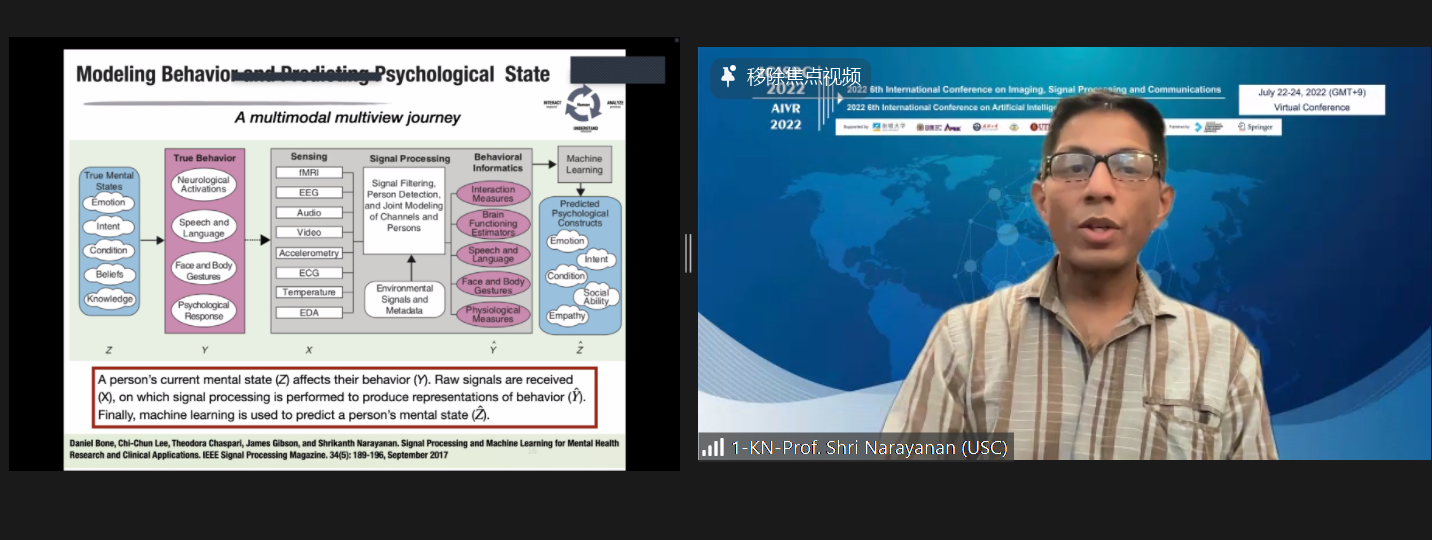
Title: Toward Trustworthy Human-centered Behavioral Machine Intelligence
Abstract: Converging technological advances in sensing, machine learning and computing offer tremendous opportunities for continuous contextually rich yet unobtrusive multimodal, spatiotemporal characterization of an individual’s behavior and state, and of the environment within which they operate. This in turn is enabling novel possibilities for understanding and supporting various aspects of human-centered applications notably in psychological health and well-being. This talk will highlight some of the advances, opportunities and challenges in gathering human-focused data and creating algorithms for machine processing of such cues. It will report efforts in Behavioral Signal Processing (BSP)—technology and algorithms for quantitatively and objectively understanding typical, atypical and distressed human behavior—with a specific focus on communicative, affective and social behavior. Examples will be drawn from health and wellbeing realms such as Autism Spectrum Disorder, Couple therapy, Depression, Suicidality, and work place behavior. It will also discuss the challenges and opportunities in creating trustworthy signal processing and machine learning approaches that are inclusive, equitable, robust, safe and secure e.g., with respect to protected variables such as gender/race/age/ability etc.

Prof. Chip Hong Chang
Fellow of IEEE and IET
Nanyang Technological University, Singapore
Biography: Chip
Hong Chang is an Associate Professor at
the Nanyang Technological University
(NTU) of Singapore. He held concurrent
appointments at NTU as Assistant Chair
of Alumni of the School of EEE from 2008
to 2014, Deputy Director of the Center
for High Performance Embedded Systems
from 2000 to 2011, and Program Director
of the Center for Integrated Circuits
and Systems from 2003 to 2009. He has
coedited five books, and have published
13 book chapters, more than 100
international journal papers (>80 are in
IEEE), more than 180 refereed
international conference papers (mostly
IEEE), and have delivered over 50
keynotes, tutorial and invited seminars.
His current research interests include
hardware security, trustworthy sensing,
anti-spoofing biometric, secure edge AI
and PQC accelerators. Dr. Chang
currently serves as the Senior Area
Editor of IEEE Transactions on
Information Forensic and Security
(TIFS), and Associate Editor of the IEEE
Transactions on Circuits and Systems-I
(TCAS-I) and IEEE Transactions on Very
Large Scale Integration (TVLSI) Systems.
He was the Associate Editor of the IEEE
TIFS and IEEE Transactions on
Computer-Aided Design of Integrated
Circuits and Systems (TCAD), IEEE
Access, IEEE TCAS-I, etc.. He also guest
edited about 10 journal special issues.
He has held key appointments in the
organizing and technical program
committees of more than 60 international
conferences (mostly IEEE). He is the
2018-2019 IEEE CASS Distinguished
Lecturer, a Fellow of the IEEE, IET and
AAIA. He was recently conferred the
Award of Excellence in Hardware Security
by the Venus International Foundation
Center for Advance Research and Design.
Title: Data Augmentation Based Backdoor for Poisoning and Watermarking of Deep Neural Networks
Abstract: The decision boundaries of lower bias complex deep neural network (DNN) are more easily overstrained by source distribution of the training dataset to perform poorly on domain shift. By increasing the size and diversity of the training dataset, data augmentation can reduce the variance of complex model to overcome the overfitting problem and increase its generalization capability. This talk will present two atypical and contrary uses of data augmentation on DNNs. While the global market capitalization of artificial intelligence (AI) product has risen tremendously in recent years, deployment of pre-trained DNN models continues to be threatened by the notorious backdoor attacks. The first part of this talk will demonstrate that a data augmentation based backdoor attack can achieve higher stealth, attack success rate, and robustness against state-of-the-art backdoor detectors. As the payoff of a well-trained proprietary DNN model is an outcome of heaving investment in computing power and labour on arduous data collection and labelling tasks, it deserves specific protection and digital rights management. Unfortunately, surrogate attacks and emerging model extraction techniques make it feasible to reverse engineer a deployed DNN model and rebuild an AI product or solution with similar quality at a lower cost than re-designing a DNN from scratch. The rampant DNN IP infringement is further exacerbated by the lack of buyer traceability to deter dishonest users from misappropriation of distributed models. The pirated model may undergo post-processing or transfer learning to fit into the attacker’s use cases to evade IP detection. To deal with this problem, a new backdoor based buyer-traceable watermarking scheme against model piracy and misappropriation will be presented in the second part of this talk.